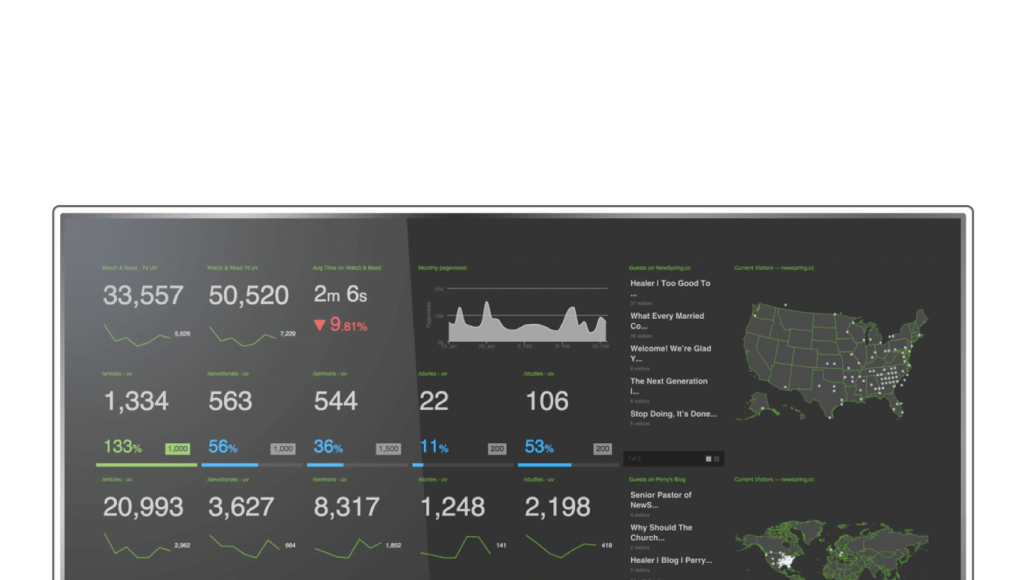
Image: Helium Sensors with Smart City Stack
This series of articles by Carlo Ratti with Daniele Belleri was first published as a catalogue for the Vitra Design Museum’s “Hello Robot” exhibition. It is republished here by permission.
PART iii – RiSKY RoBoTicS
Despite its ability to meet our needs, the idea of a robotic house still prompts some disturbing thoughts. Living within a robot-controlled house is not necessarily reassuring – probably because of the robot’s simultaneously mysterious and uncontrollable intelligence. This intelligence may be thinly concealing the looming possibility of a “betrayal” or a “hacking”, irrespective of whether the agent behind such an act is robotic or human. Surely this was what another Xerox-PARC member, the composer Rich Gold, had in mind in his essay in Cybernetics and Systems, entitled “How smart does your bed have to be before you are afraid to go to sleep at night?”
But how could our own nest manage to deceive us? We can imagine a house that plays malicious pranks on us – for example, if our at suddenly turned into a haunted mansion – or we can consider an intelligence that gathers data about us so as to implement some subtle form of blackmail. This could take the form of an “ethical house”, which would monitor your actions and could, say, result in unfavourable deals from insurance companies if you managed your own health in ways that were deemed reckless. This scenario could, in fact, become a reality in the not-too-distant future: in May 2016, in keeping with the industry’s principle of loss prevention, the insurance and risk management company Munich Re contributed to the $20 million, GV-led funding of Helium, a startup selling smart sensors that measure domestic variables such as temperature, pressure, light, humidity, and barometric pressure.
How then to deal with possible hacking and intrusions? Hacking can be carried out anywhere and everywhere, potentially involving multiple networks in obscure locations. We all know what happens when our computer gets a virus or is hacked – and crashes. But what if our very house should crash? This possibility defies conventional strategies of retaliation and protection. As the then US Defense Secretary Leon Panetta warned in 2012: given its current systems, the United States is vulnerable to a “cyber-Pearl Harbor”16 that could derail trains, poison water supplies, and cripple power grids.
How could we prevent such a scenario? One option, surprisingly, might be to promote the widespread adoption of hacking itself. Familiarity with hackers’ tools and methods provides a powerful advantage in diagnosing the strength of existing systems and can help us to design tighter security from the bottom up – a practice known as “white hat” hacking.17 Ethical infiltration enables a security team to render digital networks more resistant to attack by identifying their flaws. This could become routine practice – a kind of cyber re drill – for governments and businesses in the near future, while academic and industry research continues to focus on developing further technical safe- guards.
In general, today’s security measures take the form of autonomous, constantly vigilant digital “supervisors” – computers and code that control other computers and code. Like traditional military command- and-control protocols, they gain power in numbers and can respond swiftly to a broad array of attacks. Such a digital ecosystem strengthens checks and balances, reducing the possibility of failure and mitigating the effects of an incursion. One could imagine a house as an army of robots, each keeping track of the other, while also checking up on us.
PART iV – A cemeTeRY, AFTeR ALL , follows tomorrow.